Over the Top PTT implementations provide participating agencies the most flexibility and feature rich experience. They are network independent and work between networks so customers have much more flexibility in both network and device choices. Adding today’s carrier-based QoS offerings (from Verizon Wireless and AT&T) to Basic Over the Top PTT systems, Carrier Integrated PTT systems are lackluster in comparison. Below are some of the characteristics associated with Basic Over the Top PTT.
 Carrier Independent
Carrier Independent
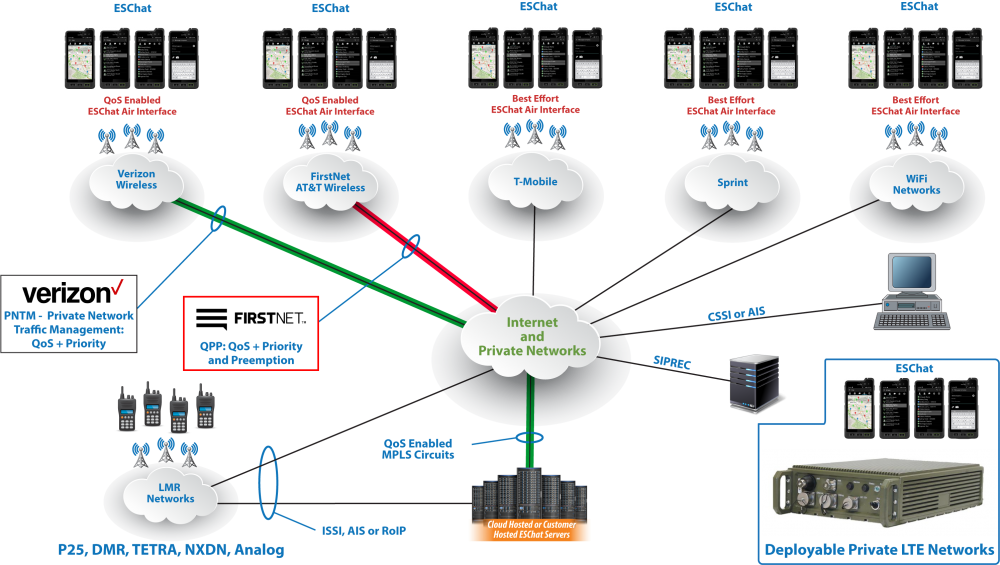
Over the Top (OTT) refers to an architecture where the PTT system is fully independent of the carrier’s wireless networks. A properly designed OTT system can communicate over traditional wireless carrier networks (Verizon, AT&T, T-Mobile, etc.) Wi-Fi networks (public or private), standard wired networks (for PC clients), and private LTE networks, including FirstNet and Deployable systems. With Basic Over the Top systems, the carrier is simply the data transportation provider and is agnostic to the PTT system or network.
Cross Network Communication
Over the Top Push to Talk systems are not subject to restrictions imposed by wireless carriers on their own PTT offerings. As such, Over the Top PTT users can span across many networks. Therefore, a large business can select the wireless carrier that provides the best coverage in each given region. Businesses benefit by gaining the best wireless coverage in each of their operating areas. User training and customer support processes also benefit as only a single set of training and support materials needs be managed. Employees that move between regions (and wireless carriers) do not need to be re-created onto a second Carrier Integrated PTT solution, rather all users are part of a consolidated PTT system.
Security
Over the Top systems are able to provide end-to-end strong encryption between mobile devices operating across multiple carriers. In this case, the OTT providers themselves are acting as the ‘carrier’ and are required to adhere to CALEA laws as they relate to lawful intercept (wiretap) orders.
ESChat network management is performed through a web-based administrative portal. ESChat customers can augment network management by interfacing with other business systems through ESChat web service APIs.